Cyberattacks are on the rise.
300%
increase in detections of advanced phishing attacks by Barracuda in 2023.
48%
of organizations experienced phishing or social engineering attacks in 2023.*
47%
of advanced phishing attacks are missed by Microsoft native security.
AI enables cybercriminals to scale attacks and avoid detection.
Preparation
AI will automate the collection and analysis of data to identify potential targets and vulnerabilities, craft emails, and generate malware designed to evade detection.
Phishing and Account Takeover
AI is used to craft more convincing and personalized phishing emails, increasing the likelihood of successful attacks.
Network Compromise
AI will automate the process of identifying and exploiting vulnerabilities in target systems while adapting in real time to the target’s responses, making attacks difficult to stop.
Lateral Movement
AI algorithms guide attackers to prioritize certain targets for lateral movement and help to determine what data is valuable before it’s encrypted.
Data Exfiltration
AI can optimize extracting and exfiltrating sensitive data, making it more challenging for security systems to detect unusual behavior patterns and circumventing traditional defenses.
Ransom Demand
After the data is encrypted and the ransom is demanded, AI can automate the interaction between the victim and the attacker.
Preparation
AI will automate the collection and analysis of data to identify potential targets and vulnerabilities, craft emails, and generate malware designed to evade detection.
Phishing and Account Takeover
AI is used to craft more convincing and personalized phishing emails, increasing the likelihood of successful attacks.
Network Compromise
AI will automate the process of identifying and exploiting vulnerabilities in target systems while adapting in real time to the target’s responses, making attacks difficult to stop.
Lateral Movement
AI algorithms guide attackers to prioritize certain targets for lateral movement and help to determine what data is valuable before it’s encrypted.
Data Exfiltration
AI can optimize extracting and exfiltrating sensitive data, making it more challenging for security systems to detect unusual behavior patterns and circumventing traditional defenses.
Ransom Demand
After the data is encrypted and the ransom is demanded, AI can automate the interaction between the victim and the attacker.
Outsmart AI with AI
- Improved threat detection and intelligence
- Superior detection efficacy of phishing attacks
- Effective in-the-moment security awareness training
- Faster incident response through automation
- Stronger application security
Improved threat detection and intelligence
Machine learning algorithms analyze email traffic and network activity to establish a company’s baseline behavior and then identify anomalies related to potential attacks, such as unusual traffic, emails, or unexpected user behavior. AI’s pattern recognition capabilities excel in identifying complex attack patterns, recognizing evolving techniques, and using predictive analysis to anticipate future threats.
Superior detection efficacy of phishing attacks
AI-powered email security leverages data from established phishing patterns to identify malicious emails that traditional gateways miss. It analyzes anomalies in email behavior, such as irregular sender behavior, while natural language processing evaluates message content for sentiment, context, tone, and potential malicious intent. The result is enhanced detection accuracy of personalized phishing attacks, including those generated using AI techniques.
Effective in-the-moment security awareness training
While traditional training regimens generally adhere to a periodic schedule, involving simulations or fabricated attacks, GenAI can help provide targeted, personalized, in-the-moment training to end users. Users will be offered tailored resources and chat support to provide context on the attack they are being targeted with. This method appeals to users and saves time for security teams, providing more effective and intuitive training.
Faster incident response through automation
Deploying AI in security operations offers faster response to threats and incidents. AI-driven systems operate more efficiently in real time, correlateing signals across attack surfaces to disable attacks sooner while reducing human error. Current applications include automating incident identification, orchestrating playbook automation, and increasing the effectiveness of SOC teams by enhancing threat detection and response.
Stronger application security
AI and machine learning improve bot detection by reducing the number of false positives typical of more traditional solutions. AI-powered application security will more accurately detect initial access and reconnaissance attempts by identifying potential zero-day attacks and alerting IT admins while automatically blocking the attacks.
The future of security lies in the fusion of human expertise and AI. The ability to analyze vast real-time datasets and identify patterns makes AI an indispensable asset in the defender’s toolkit.

Get AI-powered security from Barracuda.
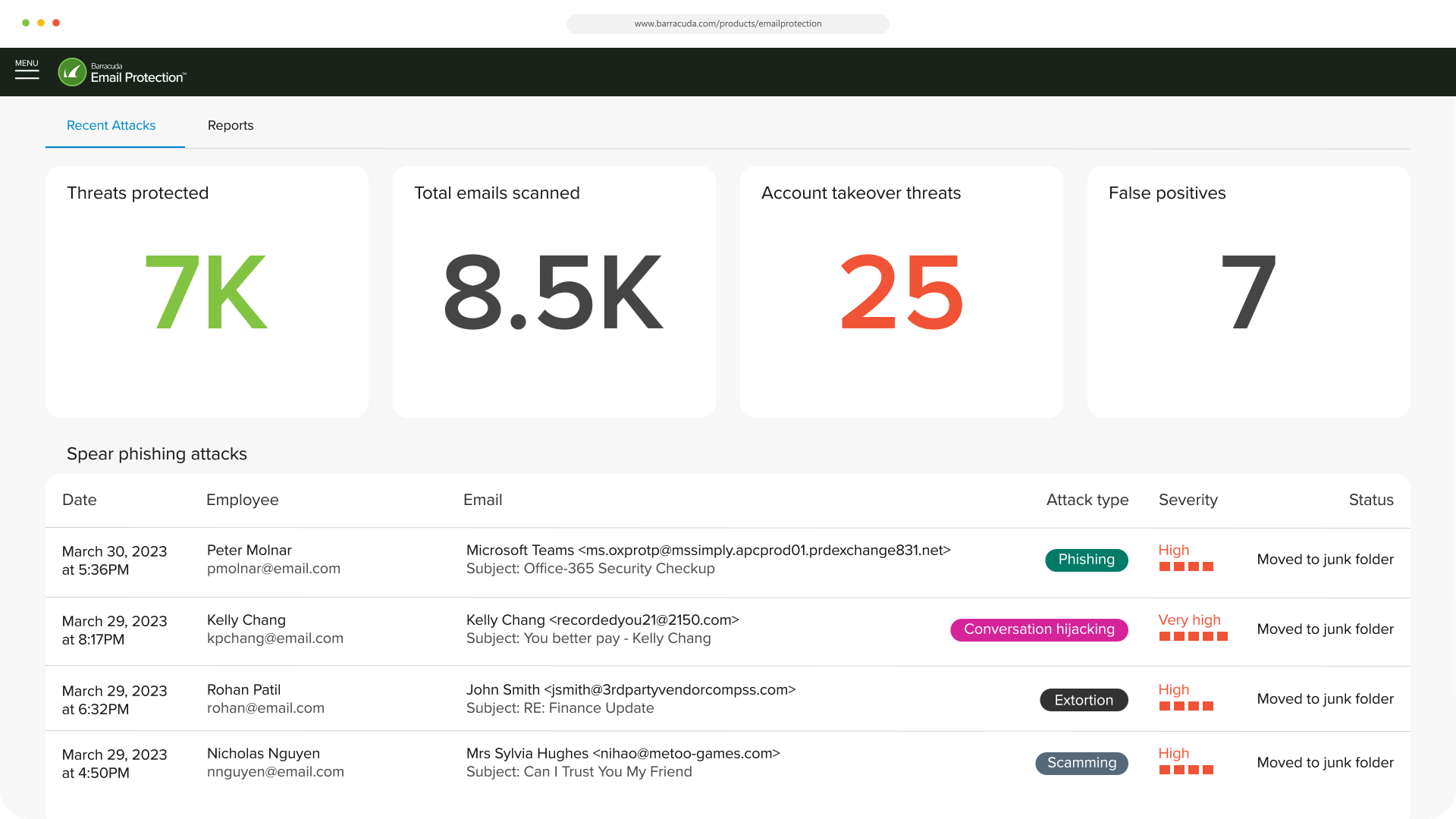
AI-powered email security
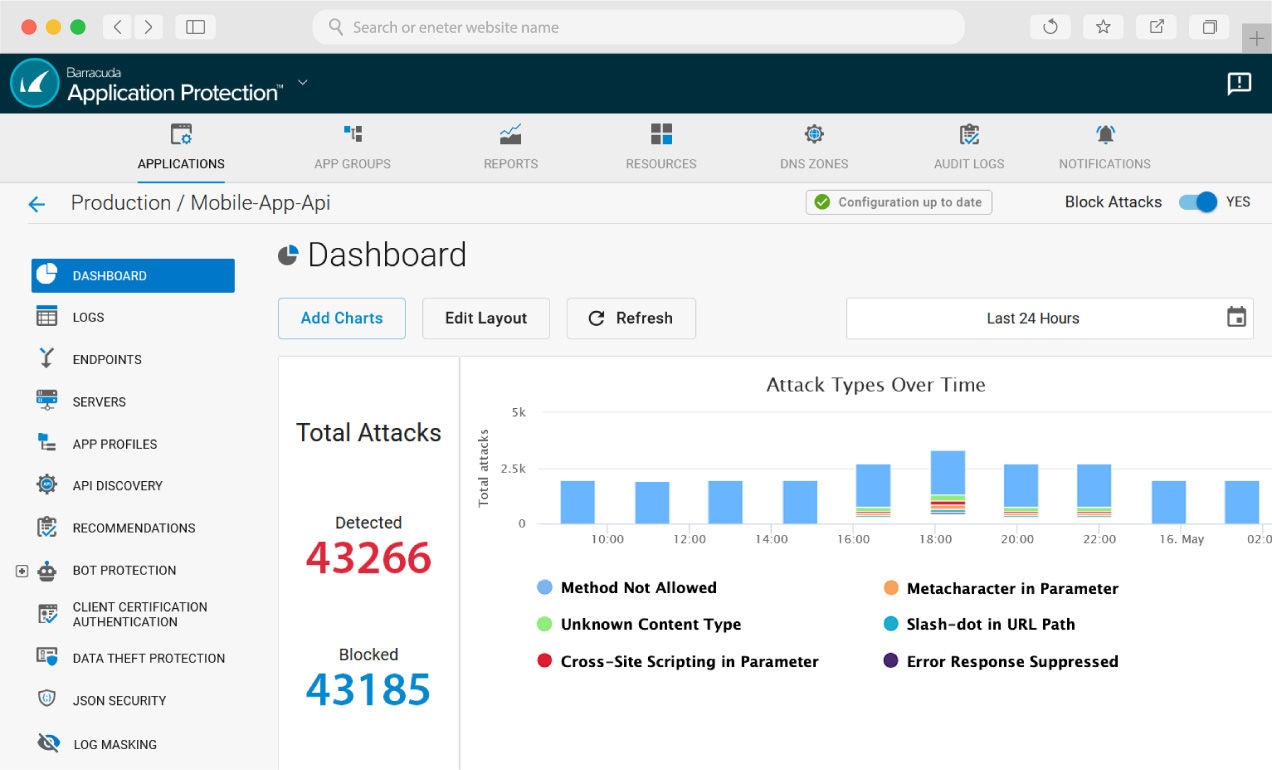
AI-powered Web Application and API Protection
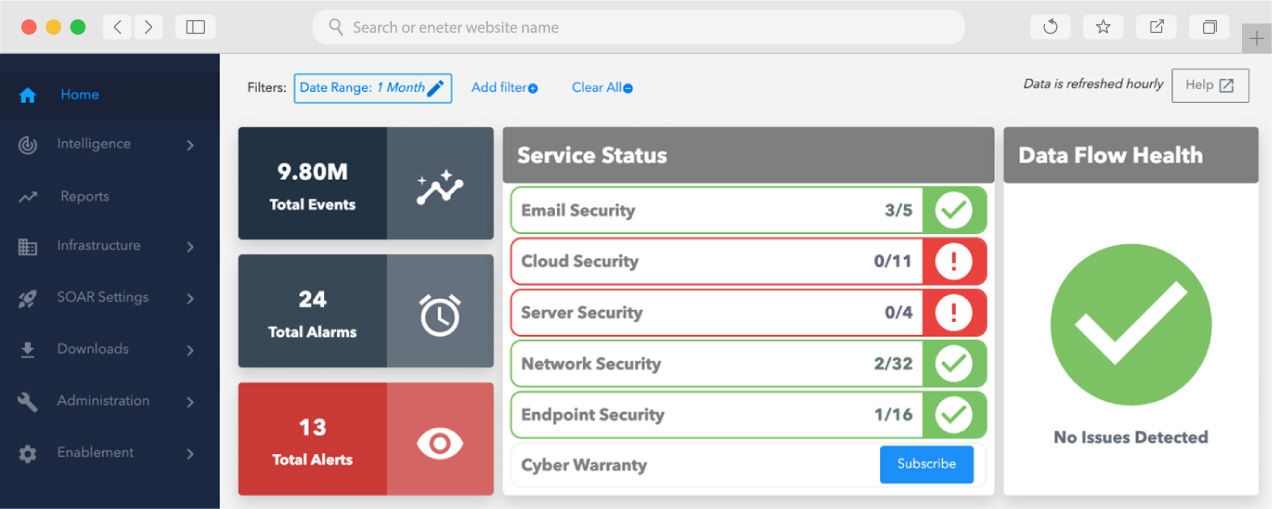
AI-powered XDR & SOC

Securing tomorrow:
A CISO’s guide to the role of AI in cybersecurity
See the impacts of ariticifical intelligence on both cyberattacks and defenses.